Note that, The X-UA-Compatible tag and header override any existing DOCTYPE. Also, the mode specified by the page takes precedent over the HTTP header.
Tag:


*#3370# - Enhanced Full Rate Codec (EFR) activation. Increase signal strength, better signal reception. It also help if u want to use GPRS and the service is not responding or too slow. Phone battery will drain faster though.
*#3370* - (EFR) deactivation. Phone will automatically restart. Increase battery life by 30% because phone receives less signal from network.
*#4720# - Half Rate Codec activation
*#4720* - Half Rate Codec deactivation. The phone will automatically restart
If you forgot wallet code for Nokia S60 phone, use this code reset: *#7370925538#
Note, your data in the wallet will be erased. Phone will ask you the lock code. Default lock code is: 12345
Press *#3925538# to delete the contents and code of wallet.
Unlock service provider: Insert sim, turn phone on and press vol up-arrow keys) for 3 seconds, should say pin code. Press C, then press * message should flash, press * again and 04*pin*pin*pin#
*#7328748263373738# resets security code. Default security code is 12345









People cannot imagine a day without their mobile phones nowadays with phones occupying a very significant place in our lives. Mobile phones are prone to damage due to their rampant usage as also many times we have observed that there is whole lot of mayhem when it is dropped in the water. Well here are the 7 useful tips for bringing your mobile phone back to normalcy after it has been dropped into the water.
Believe me, the method is a tested one.

That's it..!!
Using Wap:
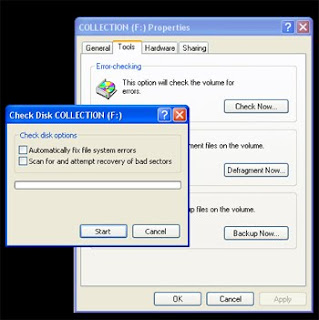
Note: Check Disk can take more than an hour to check and clean errors on your computer.
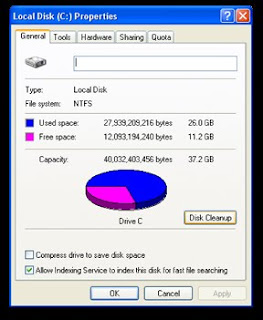
To run Disk Cleanup:
Rearrange your data (Run once a month)
Don't be shocked, but your computer can get sloppy. Your computer often breaks files side by side to increase the speed of access and retrieval. However, as files are updated, your computer saves these updates on the largest space available on the hard drive, often found far away from the other adjacent sectors of the file.
The result: a fragmented file. Fragmented files cause slower performance. This is because your computer must now search for all of the file's parts. In other words, your computer knows where all the pieces are, but putting them back together, and in the correct order when you need them, can slow your computer down.
Windows includes a Disk Defragmenter program to piece all your files back together again (if only Humpty-Dumpty had been so lucky) and make them quicker to open.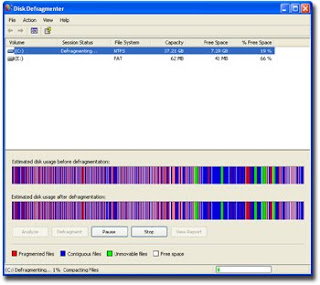
To run the Disk Defragmenter:
Make Internet Explorer run faster
The Web is a sparkling achievement of modern society. It's everywhere?from the home to the classroom. We use it to communicate, to work, to play?even to waste time when there's nothing else to do.
Yet there's nothing more frustrating than having this technical marvel at our fingertips 24 hours a day, 7 days a week, only to watch our computers access the Internet at a crawling pace. Thankfully, Microsoft Internet Explorer provides some useful options for quicker Web surfing. Let's look at these options now.
Reduce the size of your Web page history
Internet Explorer stores visited Web pages to your computer, organizing them within a page history by day. While it's useful to keep a couple days of Web history within your computer, there's no need to store more than a week's worth. Any more than that and you're collecting Web pages that will slow down your computer's performance.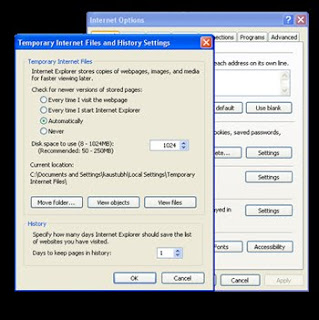
To reduce your Web page history:
Don't save encrypted Web pages
Encrypted Web pages ask for usernames and passwords. These pages scramble information to prevent the reading of this sensitive information. You can define Internet Explorer to not save these types of pages. You'll free up space by saving fewer files to your computer, as well as keeping secure information off your computer.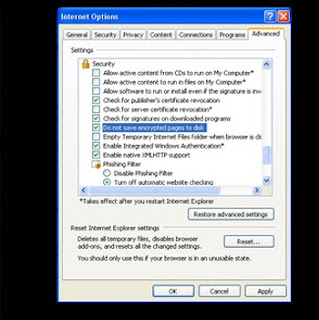
To not save encrypted Web pages:
Install antivirus and antispyware programs
Computer viruses and spyware (hidden software that gathers information about you without your knowledge or consent when you're using a computer) both reduce system performance. Computer viruses can not only reduce performance, but they can also destroy data. Any computer that accesses the Internet should have antivirus and antispyware programs installed.

Take into consideration these tips and you will have a successful site for years to come.
Why it Doesn't Matter How Your Website Looks If You Have No Traffic Coming to It
When people get started on the Internet for the first time they have the wrong idea on how to market. They worry too much about how their website looks and they probably don't even have any traffic coming to it. The lesson that I have learned from my years online is that you do not have to be fancy when building a website.
The first thing you have to focus on is finding a way to get traffic to your website. Once you are able to do this then you can dedicate the time to upgrading the website and make it look better but it really does not matter when you're not getting any traffic. You can actually make a website that is captivating and at the same time simple instead of fancy.
You would not believe how many people worry about how the website looks and the last thing they do is try to get ways to drive traffic to it. I have seen many websites that may not be the best but they are still being successful because of the amount of traffic that they drive to it.
As I mentioned before it is good to have a good-looking website but is not good to waste all your time trying to do this because then you will only be left with a website with no traffic. It has to be a balance between having traffic to your page and dedicating time to creating a better looking website. My suggestion is when you first get started the last thing in your mind should be how it looks instead it should be how to drive more traffic to it. There will be many ways for you to promote your website on the Internet just make sure that the method you choose is an effective one.

 How Obama Will Use Web Technology
How Obama Will Use Web Technology


Every country in the world is going to be the victim of power crisis. But developing countries like India are going to face real problems very soon if we do not conserve power. So here are some basic tips which will help to reduce the power consumption in daily life.
Power saving tips:
Air conditioners
Keep the temperature at 23 degrees which is sufficient normally.
Use coolers instead of air conditioners.
Keep doors to the air conditioned area closed so less power is utilized.
Cell Phones
Use car chargers instead of plugging the charger into a wall socket at home.
Do not keep your phone for charging overnight it can also damage your battery by over charging.
When using the computer, charge your phone using the USB port (if possible).
This uses the power from the PSU-which may otherwise be wasted.
Desktop
Use LCD (TFT) monitors or TVs instead of CRTs whenever possible because CRT consumes more power.
If you aren't keen on playing games, avoid installing a graphics card, especially models with liquid cooling solutions.
Avoid over clocking your processor or graphics card if not necessary.
Set the monitor to automatically shut off or go in standby mode when idle.
Turn the monitor off when your computer is unattended.
Reduce the monitor’s luminosity till the point it is visible.
Laptops
Reduce the luminance of the back light.
Keep the wireless switch turned off if you are not connected to a network.
Charge your laptop batteries only after the battery is fully drained.
Use the balanced mode in power options which will help to utilize the processor only when needed.
General
When alone, use stereo headphones instead of Hi-Fi speakers.
When family members dine or watch TV in the same room, the need for lights and fans elsewhere doesn't arise so ensure that all other lights and fans are switched off.
Instead of keeping the television, music system, printer, scanner, speaker and any other appliance and device, on standby mode, switch them off completely. You can remove the power plug of devices which are not used from the socket and conserve power.
Keep a regular check on your monthly bill to curb power consumption.
So remember the above tips whenever you are dealing with electricity. This can help the country to overcome the power crisis to an extent and also you will be benefited by saving cash paid for your electricity bills.